Consider how convenient it would be for everyday battery-free devices to have similar functions to the Wi-Fi enabled shelf devices used regularly, like smartphones and laptops.
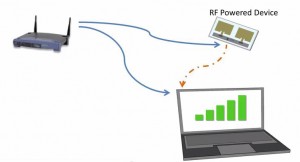
By powering battery-free devices with an embedded sensor that absorbs signals from the surrounding Wi-Fi infrastructure, passive devices are activated with a Low-WiFi “carrier wave” that allows them to communicate, track activity and store information without altering its hardware. (more…)

 Netgear WN604
Netgear WN604